These Phishing Tactics Disguised as ‘Fun’ on Social Media. Here’s What to Look For
Everyone reading that post doesn’t need to know the name of the street you grew up on.
James Martin/CNET
If you’re on any social media platform, you’ve likely encountered a post stating something like, “Your preppie name” (or your pirate name, your indie band name, etc.) “is the street you lived on as a child plus the name of your first pet.” The often hilarious results number into the thousands in the comments.
Facebook quizzes and questionnaires might seem like harmless fun, but the comments sections under these posts are a goldmine of potential passwords served up buffet-style for shady cyberthieves. Not on social media? Unfortunately, you’re still at risk via text messages, phone calls and email. This manipulative tactic is a more recent twist on a classic cyberattack known as phishing. Here’s what you need to know to protect yourself.?
What is phishing??
Phishing is a way that malicious hackers make use of human error — typically by preying on the gaps in a person’s tech savvy — to gain access to private or sensitive information. Instead of a brute force attack, the cybercriminal poses as a familiar face or legitimate organization issuing a call to action that sounds either fun or urgent. After you’re lured into a false sense of security and take the bait, the phisher nets your sensitive information.
Cybercriminals exploit facets of human nature like fear, greed, curiosity, helpfulness and sense of urgency, according to Terranova Security. You’ve likely gotten one of those infamous voicemails about your car’s soon-to-be-expired extended warranty. You probably know that the deposed Nigerian prince who needs your credit card information so he can pay you back a million dollars is a cybercriminal. But this kind of scammer may pose as something more everyday, like someone from your car dealership.
What does phishing look like on social media?
Social media phishers post innocent-looking, simple questions on social media asking about your first job or first car. These posts may seem lighthearted, but these are often common security questions — and the comments section is rife with answers.?
These question-game prompts might read like:?
- Who remembers their first grade teacher? Let’s celebrate our educators!?
- Nobody’s first car was a Toyota. Prove me wrong!?
- Name a movie you can watch over and over again.
- If you could go anywhere right now, where would you go??
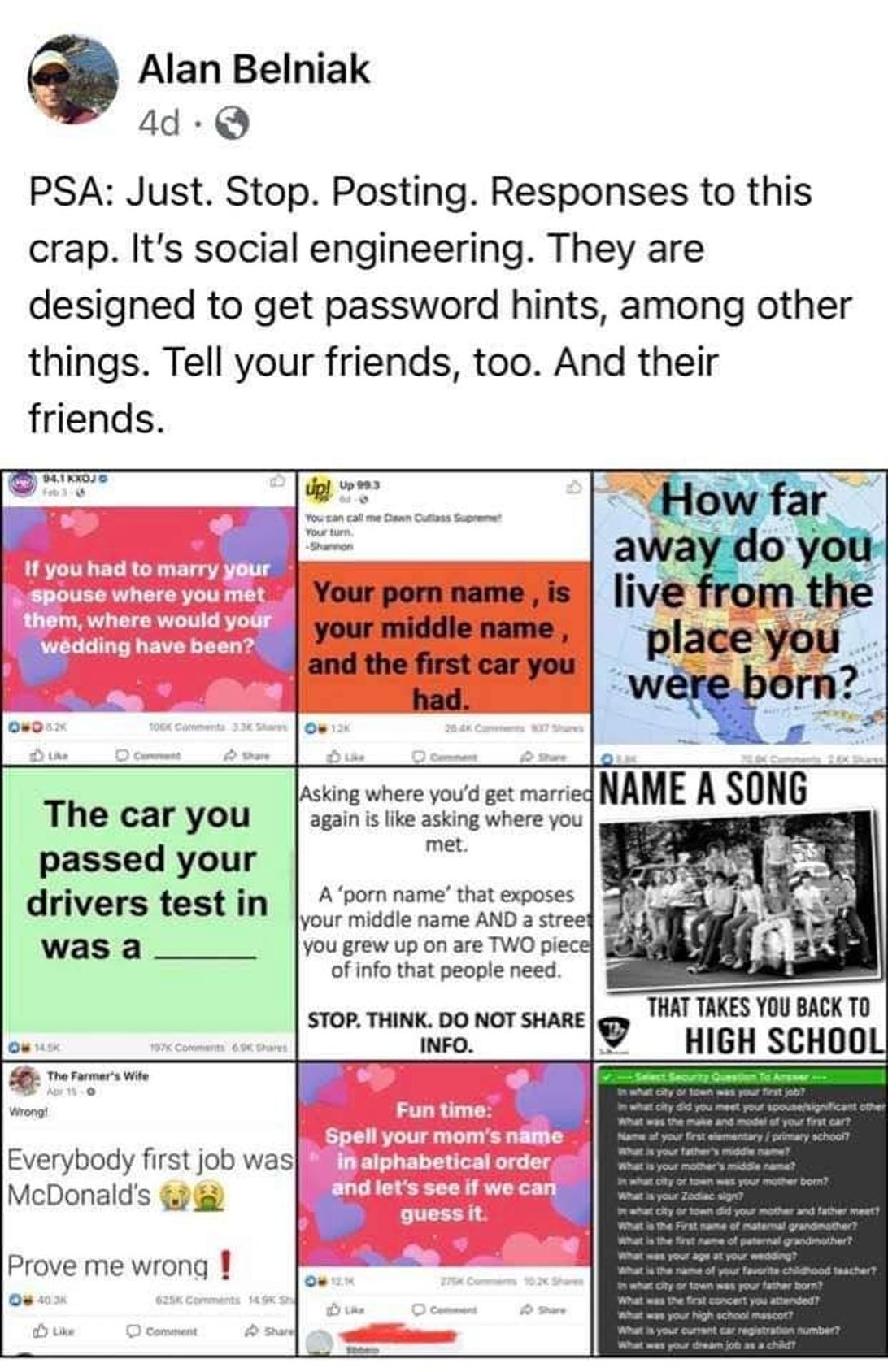
Alan Belniak posted an example of phishing schemes disguised as games on Facebook.
Screenshot by CNET/Alan Belniak Facebook
It’s not a guarantee that every question game post you see was crafted by a cybercriminal, but these posts are dangerous regardless of the intentions of the person posting them. The posts are often public, and there’s no way to control who’s reading the comments.
The problem is pervasive on Facebook, but extends to other social media as well. Quizzes, surveys on Twitter and Instagram, as well as “get to know you” videos on TikTok can be exploited by cybercriminals working alone or in groups.
Where else am I vulnerable to phishing??
A few more common types of phishing include emails asking you to click a link to redeem a prize, or a text warning you that your bank account has been compromised.
These messages are meant to manipulate your emotions — the fear of your vehicle breaking down and having no coverage, the excitement of winning a contest or the possibility of some extra money or the panic that your hard-earned money is at risk.?
The thread tying these messages together is a sense of urgency. If the messages demand that you supply your Social Security number, a password or an account number or click a link right now, you’re likely the recipient of a fraudulent scam.

Social media is rife with phishing schemes.
Angela Lang/CNETHow do I protect myself from phishing attacks?
Phishing scams are all too common, but there are steps you can take to stay safe. Here are a few ways you can shut down phishing attempts.?
- Don’t hand out sensitive information on social media. Just don’t. It’s tempting to fill out a “30 random things to know about me” or join the conversation about what your first car was, but the risk of that information being used against you is far greater than it may seem. Don’t answer the prompts, and don’t share those prompts with others.
- Check the source. Who or what organization is sending you this message? Have you had contact with them before? Does it make sense that they’re reaching out to you? Verify any giveaways from other sources, and if you’re unsure, don’t take the bait.
- Slow down. Attackers using social engineering bank on a panicked reaction instead of a clear-minded response. Consider whether the message makes sense. For example, would your manager ask you to disclose your password via text — or at all??
- Look for inconsistencies. The way a message is written will tell you a lot about the authenticity of it. Are words misspelled or spaced strangely? Hover over any links without clicking on them — does the linked website even match what the email is talking about? Many phishing scams don’t hold up under scrutiny.
- Flag, report and block spam. If you get a suspicious email or text message, mark it as spam, report it to your IT department or delete it.?
For more on information security, check out how to get started with a VPN and browser settings you should change to protect your privacy.